Despite early reports that there was no use of National Security Agency-developed exploits in this week’s crypto-ransomware outbreak, research released by Cisco Talos suggests that the ransomware worm known as “Bad Rabbit” did in fact use a stolen Equation Group exploit revealed by Shadowbrokers to spread across victims’ networks. The attackers used EternalRomance, an exploit that bypasses security over Server Message Block (SMB) file-sharing connections, enabling remote execution of instructions on Windows clients and servers. The code closely follows an open source Python implementation of a Windows exploit that used EternalRomance (and another Equation Group tool, EternalSynergy), leveraging the same methods revealed in the Shadowbrokers code release. NotPetya also leveraged this exploit.
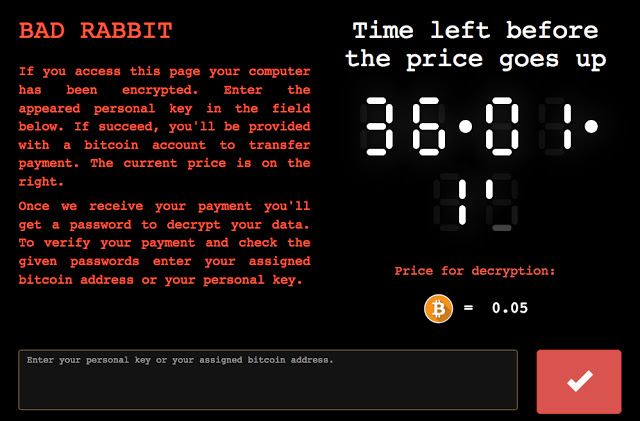
Bad Rabbit, named for the Tor hidden service page that it directs victims to, initially landed on affected networks through a “driveby download” attack via compromised Russian media websites. Arriving disguised as an Adobe Flash update, Bad Rabbit has multiple ways of spreading itself across networks. It can exploit open SMB connections on the infected Windows system, and it can also exploit the Windows Management Instrumentation Command-line (WMIC) scripting interface to execute code remotely on other Windows systems on the network, according to analysis by EndGame’s Amanda Rousseau. And the malware has a collection of hard-coded usernames and passwords, as Rousseau and researcher Kevin Beaumont noted.
But according to Talos, Bad Rabbit also carries code that uses the EternalRomance exploit (patched by Microsoft in March), which uses an “empty” SMB transaction packet to attempt to push instructions into the memory of another Windows computer. In unpatched Windows 7 and later Windows operating systems, the exploit can use information leakage returned by the exchange to determine if it is successful; on older systems, a different version of the same exploit is used but may crash the targeted computer’s operating system in the process.
